
Since SAP is a single software application used by many employees in a company, SAP role and authorization management is essential for a sound and efficient use.
Depending on the department in which the user works, or the hierarchical level at which he/she is located, the roles and authorizations of the user will be different, but especially adapted to his/her daily tasks.
In this article, we will see together what is a role and the access to the functionalities it allows/does not allow, how to manage it and also how to assign it to a user. Then, we will develop together how to analyze and correct user authorization problems.
What an SAP role is?
To start simply, an SAP role allows you to define the authorizations of one or more users.
In addition, an SAP role can be identified by three axes:
The SAP functional transaction provides access to the launch of a functionality, which can be standard or specific.
The authorization object allows access to certain specific data. Let's take the example of a list of production orders from two factories belonging to the same company. The authorization object could, for example, restrict access to the production orders of only one factory.
In addition, SAP distinguishes between two different types of roles: the individual role and the composite role.
Individual role
The individual role corresponds to the first level, the base of the roles. It allows the collection of several functional transactions and/or authorization objects.
Composite role
The composite role simply represents a role that combines several individual roles. The management of authorizations is, therefore, simpler and faster.
Each has its advantages and disadvantages. Depending on the situation, in some cases it will be preferable to use an individual role, in others a composite role.
Note: once the role has been created, there is no longer the possibility of converting an individual role into a composite role, or vice versa. However, it will still be possible to modify its contents.
SAP roles and authorizations - Assigning roles
Once the roles are defined, it is necessary to assign them to the users according to their profiles. Each user can have one or more roles (individual role or composite role).
This happens at the user master record level. Indeed, to assign roles, use the functional transaction SU01:
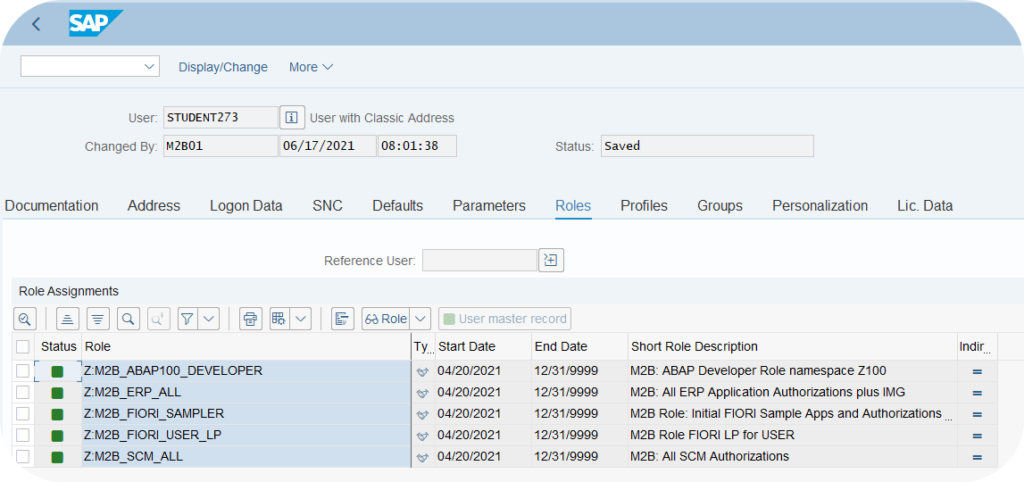
Note that it is also possible to assign roles to a user temporarily by indicating a start and end date.
Note: In the vast majority of companies, a process for adding SAP roles is provided. Therefore, please carefully follow the process (if any) set up by the company.
In addition, it is also possible to assign roles in mass to several users via standard tools such as LSMW, SHDBECATT etc...
SAP roles and authorizations - Managing SAP roles and authorizations
Indeed, since SAP role and authorization management is a critical part of a company's processes, it is usually managed by a dedicated administrator.
The management of individual roles is done via the functional transaction PFCG. Moreover, it can be split into three main parts (Menu, Authorizations and User):
In the "Menu" tab, you will find the list of transactions that the role makes accessible. It is also possible to manage the tree structure with the creation of folders, subfolders...
In the "Authorizations" tab, you will find the associated authorization objects and their values. The values of the configured authorization objects will therefore be accessible via the role in question.
Finally, the third important tab is the "User" tab. This is where the administrator can assign the role to certain users. This possibility comes in addition to the one seen previously (role assignment via the user management SU01 functionality).
Composite role management is somewhat different given its main purpose: to group together existing individual roles.
The transport of the roles
Once the roles have been created, they must be made active. It is important to note that roles are transported from one system to another. Therefore, they are first created in the development system, then transported to the test system and finally to the production system.
The transport of roles is also done via the functional transaction PFCG. There are then two options, transport role by role or perform a bulk transport of multiple roles. Once the transport functionality is executed, the request is created and will thus be able to be transported, as in a "classic" customizing.
SAP roles and authorizations errors
Many users have already faced this message:
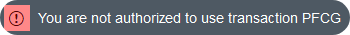
Indeed, this message, rather explicit, indicates that the user does not have the necessary role to access the functionality proposed by the functional transaction entered.
Or this one:
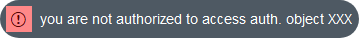
In addition, this message means that the operation performed within a transaction is not authorized for the user concerned. Let's take the case of company X, with two production sites S1 and S2. The purchasing department employee of production site S1 can access the functional transaction of the order list, but can also be restricted to those of S1 only.
In both cases, it is an error in SAP roles and/or authorizations. It is possible that this blocking message is voluntary or not. If it is voluntary, it means that the user's function or position does not allow access to the desired functionality. If it is voluntary, it may be due to an error made by the SAP administrator when assigning roles, or due to a change in function that was not taken into account. Indeed, the roles remain statically assigned to the user. Any change must be done manually.
How to analyze an authorization error?
In the event that the user is faced with an authorization error message and this is not justified, an analysis is required.
This will allow you to understand what is blocking and thus, determine with ease the missing roles and/or authorization objects.
Therefore, once the user stalls on the error message, the user can initiate the functional transaction SU53: Display authorization data. It may look like this in the context of an authorization error:
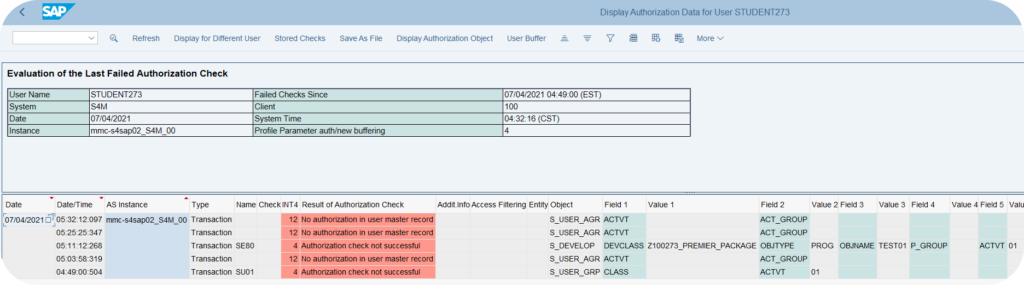
This explicitly indicates which authorizations are missing. The SAP administrator is then able to use different tools (e.g. functional transaction SUIM) to determine the missing role(s) that include these authorizations.
How to get around an authorization error?
If you have the authorizations assigned to SAP consultants, then you are able to bypass an authorization error. This is made possible by debugging.
The first step is to start the SE37 functional transaction and run the AUTH_CHECK_TCODE Function Module.
Then add a breakpoint at the line "if sy-subrc = 0":
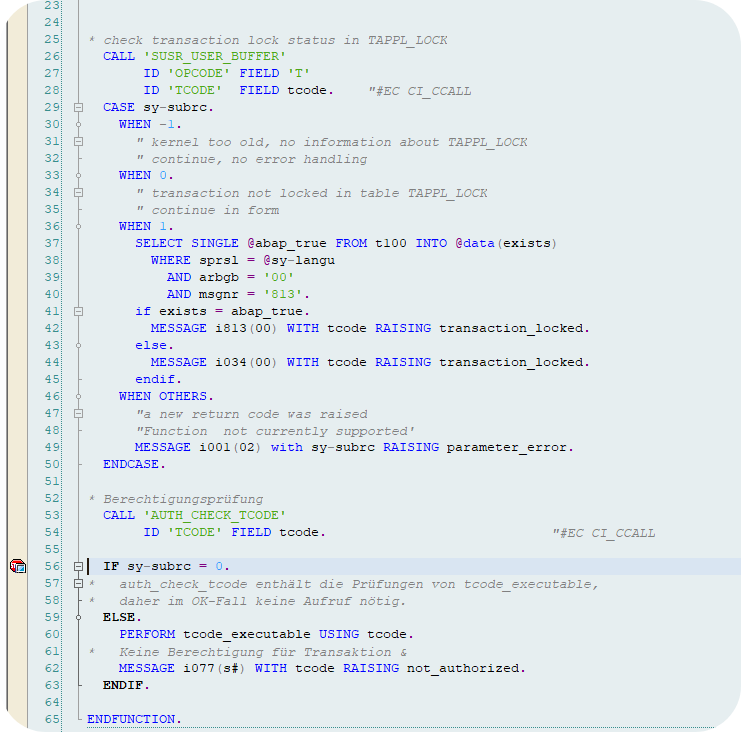
If the variable sy-subrc = 0, in this case there is no authorization error. If, on the other hand, sy-subrc is different from 0, then there is an authorization error. And it is precisely this condition that interests us.
Change the value of the sy-subrc variable to 0 and run:
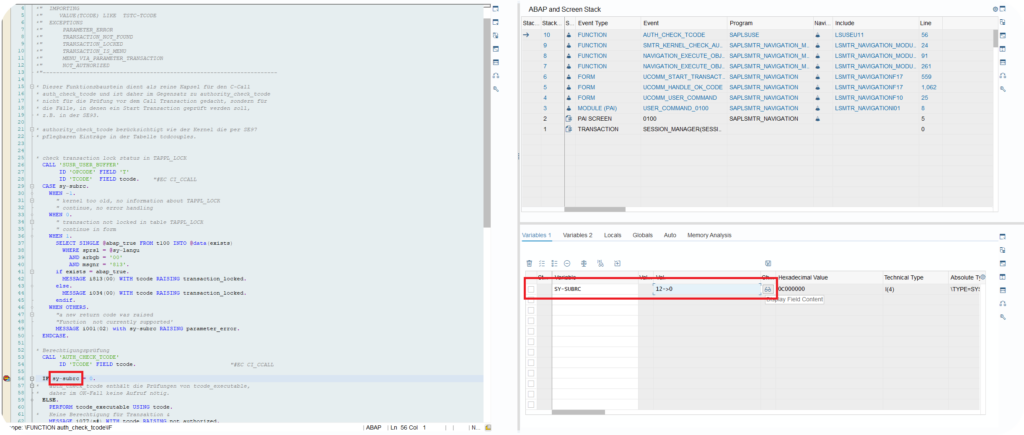
Access to the functionality is thus possible and the bypassing of the error message has taken place. However, this somewhat "illegal" technique only works temporarily and is not permanent. It should only be used in case of urgent need.
Would you like unlimited access to our entire SAP training library? Test our training platform free of charge for a 7-day trial period.

Pierre Balbinot
SAP functional consultant, EAM (Enterprise Asset Management) and PP (Production Planning) expert.







Kumar
It is very useful and helpful and amazing explanation. Could please explain in detail about su53 and stauthtrace
brisa
Muy buena explicacion. Estoy aprendiendo mucho.
keyusertraining@gmail.com
Gracias 🙂